1 Response2 Importance of MFA
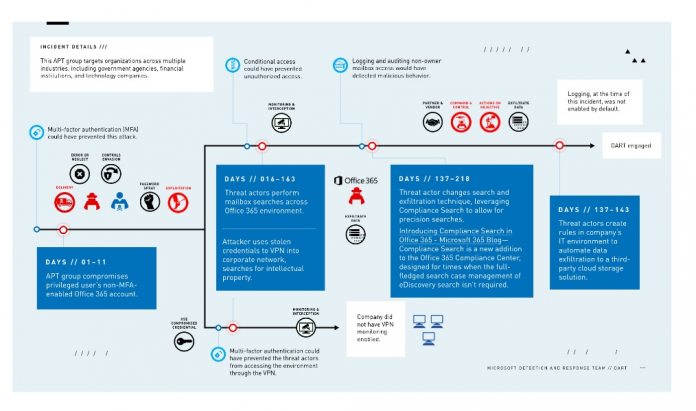
Among the attackers was a hacking group with state backing that had been stealing email and data for 245 consecutive days. DART says the attack was an advanced persistent threat (APT) campaign. The hacking group stole gained admin credentials and entered the network of an unnamed customer. Microsoft first announced the Detection and Response Team a year ago. The company will publish sporadic reports detailing DART’s work to better protect enterprise users. Redmond says the reports will help to keep customers on their toes when combatting cyberthreats. Its first report details says the customer hit by six simultaneous attacks was not using multi-factor authentication (MFA). If it was in place, MFA would have thwarted the state-sponsored hacking group and protected sensitive data and emails.
Response
The customer sought Microsoft’s help when it was unable to remove the APT attack from its network. DART intervened when the attack was ongoing for 243 days. On the day the Detection and Response Team arrived, the attacker was removed. However, the team also discovered five other ongoing threats. “This investigation lasted more than seven months and revealed a possible compromise of sensitive information – pertaining to the victim and the victim’s customers – stored in Office 365 mailboxes. 243 days after the initial compromise, DART was then brought in to work alongside the incident-response vendor and the company’s in-house teams,” Microsoft says. “DART quickly identified targeted mailbox searches and compromised accounts, as well as attacker command-and-control channels. DART also identified five additional, distinct attacker campaigns persisting in the environment that were unrelated to the initial incident. They discovered these attackers had entered the environment even earlier to establish access channels (i.e., back doors) for later use as needed.”
Importance of MFA
Yesterday, we reported on a presentation at the recent RSA Security Conference that showed over 1.2 million Microsoft accounts are compromised because they don’t have MFA in place. This means 0.5% of Microsoft accounts are hijacked each month. RSA said 40% of that 0.5% (480,000 accounts) were simply compromised by a standard password spraying method during January. Attackers would try to sign in across a vast number of accounts with some statistically likely passwords. Nearly half a million got a hit.